Overview
In this post I will describe a technique for synchronising a hashed password from ForgeRock IDM to DS.Out of the box, IDM has a Managed User object that encrypts a password in symmetric (reversible) encryption. One reason for this is that sometimes it is necessary to pass, in clear text, the password to a destination directory in order for it to perform its own hashing before storing it. Therefore the out of the box synchronisation model for IDM is take the encrypted password from its own store, decrypt it, and pass it in clear text (typically over a secure channel!) to DS for it to hash and store.
You can see this in the samples for IDM.
However, there are some times when storing an encrypted, rather than hashed, value for a password is not acceptable. IDM includes the capability to hash properties (such as passwords) not just encrypt them. In that scenario, given that password hashes are one way, it's not possible to decrypt the password before synchronisation with other systems such as DS.
Fortunately, DS offers the capability of accepting pre-hashed passwords so IDM is able to pass the hash to DS for storage. DS obviously needs to know this value is a hash, otherwise it will try to hash the hash!
So, what are the steps required?
- Ensure that DS is configured to accept hashed passwords.
- Ensure the IDM data model uses 'Hashing' for the password property.
- Ensure the IDM mapping is setup correctly
Ensure DS is configured to accept hashed passwords
This topic is covered excellently by Mark Craig in this article here:
I'm using ForgeRock DS v5.0 here, but Mark references the old name for DS (OpenDJ) because this capability has been around for a while. The key thing to note about the steps in the article is that you need the allow-pre-encoded-passwords advanced password policy property to be set for the appropriate password policy. I'm only going to be dealing with one password policy - the default one - so Mark's article covers everything I need.
(I will be using a Salted SHA-512 algorithm so if you want to follow all the steps, including testing out the change of a user's password, then specify {SSHA512} in the userPassword value, rather than {SSHA}. This test isn't necessary for the later steps in this article, but may help you understand what's going on).
Ensure IDM uses hashing
Like everything in IDM, you can modify configuration by changing the various config .json files, or the UI (which updates the json config files!)
I'll use IDM v5.0 here and show the UI.
By default, the Managed User object includes a password property that is defined as 'Encrypted':
We need to change this to be Hashed:
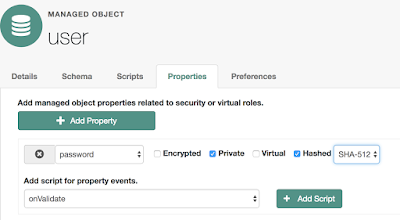
And, I'm using the SHA-512 algorithm here (which is a Salted SHA-512 algorithm).
Note that making this change does not update all the user passwords that exist. It will only take effect when a new value is saved to the property.
Now the value of a password, when it is saved, is string representation of a complex JSON object (just like it is when encrypted) but will look something like:
{"$crypto":
{"value":
{"algorithm":"SHA-512","data":"Quxh/PEBXMa2wfh9Jmm5xkgMwbLdQfytGRy9VFP12Bb5I2w4fcpAkgZIiMPX0tcPg8OSo+UbeJRdnNPMV8Kxc354Nj12j0DXyJpzgqkdiWE="},
"type":"salted-hash"
}
}
Ensure IDM Mapping is setup correctly
Now we need to configure the mapping.
As you may have noted in the 1st step, DS is told that the password is pre-hashed by the presence of {SSHA512} at the beginning of the password hash value. Therefore we need a transformation script that takes the algorithm and hash value from IDM and concatenates it in a way suited for DS.
The script is fairly simple, but does need some logic to convert the IDM algorithm representation: SHA-512 into the DS representation: {SSHA512}
This is the transformation script (in groovy) I used (which can be extended of course for other algorithms):
String strHash;
if (source.$crypto.value.algorithm == "SHA-512" ) {
strHash = "{SSHA512}" + source.$crypto.value.data
}
strHash;
This script replaces the default IDM script that does the decryption of the password.
(You might want to extend the script to cope with both hashed and encrypted values of passwords if you already have data. Look at functions such as openidm.isHashed and openidm.isEncrypted in the IDM Integrators Guide).
Now when a password is changed, the password is stored in hashed form in IDM. Then the mapping is triggered to synchronise to DS applying the transformation script that passes the pre-hashed password value.
Now there is no need to store passwords in reversible encryption!
